Now I will explain how Event Log Explorer works with disk images. If you have a disk image from an examined computer, you should mount it as a disk. If you have a real disk, you can just connect it to your PC.
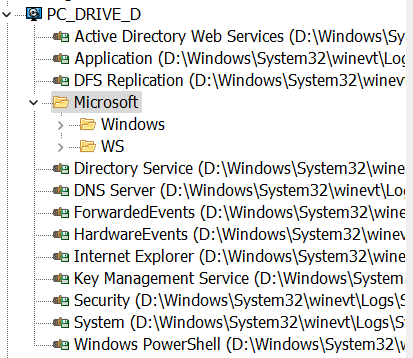
Let’s consider that you already mounted a disk that contains Windows folder of the examined PC. Now you can create a virtual (“imaged”) computer in Event Log Explorer. Select Forensics->Add Imaged Computer from the main menu. Event Log Explorer will try to detect your disk, but you can input the path to Windows folder manually. You should also type a friendly name of this computer in the Tree and press Ok.
The computer will be added to the tree as a general computer, and you can use Event Log Explorer with this virtual computer exactly like you work with the real computers!
You may think that Event Log Explorer just opens files from \Windows\System32\winevt\Logs\, but it does much more. When you just open a foreign even log file, you can often see the description rendering issues (The description for Event ID (Event) from source (Source) cannot be found). These issues occur because the event log file doesn’t contain the description messages. Even descriptions are rendered based on the installed components, and if the required component is missing, you will see the “description not found” message.
Event Log Explorer tries to emulate the live system. It reads the registry files (\Windows\System32\config\SOFTWARE and \Windows\System32\config\SYSTEM), builds a log tree, detects the location of the required description components, and then reads log files and renders descriptions messages. From the user’s point of view, you are just working with the local event logs.
Download Event Log Explorer Forensic Edition to work with disk images the same way as you work with the live computers!