Looking for a solid solution to unravel computer-stored evidence? Need a deeper insight into what’s happening on your PC or a suspect’s device, looking to restore or crack an essential password? Check out this brief review of unheralded yet powerful forensic tools.
The most common definition of computer forensics is the procedure of detecting and analyzing evidence collected from digital media, i.e. hard drives, portable devices, etc. Digital evidence should be handled carefully. Incapable hands may ruin crucial data so it becomes incomplete, compromised or unfit for further investigation. In order to help automate forensics, the computer science and software industry has come up with a plethora of professional programs. Police departments, investigation agencies and enterprises across the globe employ IT forensic tools at scale and face an overchoice of available solutions.
Computer forensics embraces different software categories. Broadly defined, it not only includes file viewers/analysis and disk and data capture tools, but also email analysis, registry forensics, network and database forensics, event log analysis, password recovery, mobile device analysis and other solution types.
Some of these, like EnCase and FTK, are globally acknowledged within the forensics community and power users. EnCase encompasses a whole suite of digital investigation solutions. These include products for forensics, e-discovery, cyber security and security analytics purposes. Data restored by EnCase have been used as evidence by multiple court systems, e.g., in the cases of the BTK Killer and the murder of Danielle van Dam.
FTK by AccessData also fits perfectly into forensic experts’ inventory. FTK Imager, a well-known data preview and imaging program, enables the user to analyze files and folders on local HDDs, network drives, and CDs/DVDs.
Other tools reveal and prove great technological potential, taking ever growing popularity among dedicated experts. And we’d like to take a closer look at a few more forensic solutions, highly recommended to add to your computer forensic arsenal. A disclaimer: we are rolling out the tools in random order so there is no rating associated with the review.
Tools
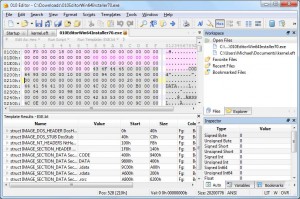
010 Editor
010 Editor is a professional text/hex editing software program by SweetScape.
The program allows you to edit any file, drive or process on the computer. Using binary templates, 010 Editor can help parse a binary file into an intelligible data structure. The software includes standard editing functionality with Cut, Copy and Paste commands, as well as support for large files and unlimited Undo/Redo actions.
010 is, in fact, a suite of editing tools. The Text Editor works with text files, XML, HTML, Unicode, UTF-8 files, C/C++ source code, etc. The Hex Editor helps the user to edit binaries and interpret binary data. The Process Editor investigates and modifies memory in running processes. The Disk Editor scans your hard drive, memory keys, flash drives, and CD-ROMs for issues, and provides immediate troubleshooting. 010 Editor allows you to analyze and edit binary files with advanced tools: Full Find, Replace, Find in Files, and Replace in Files functionality for various data types. You can also perform binary comparison, count byte occurrences and visualize data.
Event Log Explorer
Event Log Explorer by FSPro Labs is an advanced software solution for event analysis. The tool provides a deep insight into Microsoft Windows/Windows Server system logs, and covers all aspects missed by the standard Event Viewer.
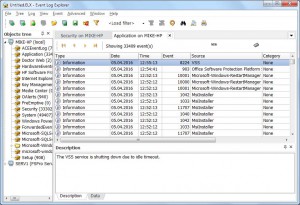 The program collects valuable evidence by reviewing events registered by the operating system.
The program collects valuable evidence by reviewing events registered by the operating system.
Users can consolidate events from multiple sources (event logs or files) into a single view – a dramatically important feature for timeline analysis. You can filter events by any relevant criteria using predefined filters or ample custom options, including regular expressions for event description.
Event Log Explorer provides direct access to EVT and EVTX files (without Windows API). This feature enables the user to view even corrupt event logs or read EVTX files under Windows XP.
In case you need to match event logs with other forensic tasks (e.g. timeline analysis), Event Log Explorer offers the Export Events feature. Events can be exported to multiple formats including HTML, Excel or text.
When you work with event log files, a computer may be lacking text descriptions of analyzed events. Event Log Explorer enables the user to retrieve event descriptions from another source.
Another forensic issue solved by this software is time correction. In the course of an investigation, you may encounter event logs from different time zones. The time zone correction feature helps you make necessary modifications and unify collected data.
Event Log Explorer fits a broad audience, including IT forensics, system administrators, security audit agents, in-house R&D, etc.
ElcomSoft solutions
ElcomSoft presents a product line aimed at forensic experts, law enforcement, military, and intelligence agencies. One of ElcomSoft’s core competencies is password cracking.
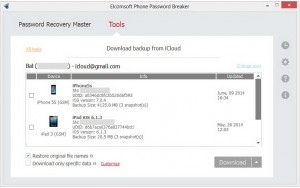 The Password Recovery Bundle enables authorized organizations and individuals to unlock disks, encrypted files and documents protected with publicly available applications. Another solution by ElcomSoft – iOS Forensic Toolkit – enables the user to acquire precise images of iOS devices. You can get access to all passwords and encryption keys on a select device and decrypt the image of its file system. iOS Forensic Toolkit also provides a passcode retrieval option to access passcode-protected evidence.
The Password Recovery Bundle enables authorized organizations and individuals to unlock disks, encrypted files and documents protected with publicly available applications. Another solution by ElcomSoft – iOS Forensic Toolkit – enables the user to acquire precise images of iOS devices. You can get access to all passwords and encryption keys on a select device and decrypt the image of its file system. iOS Forensic Toolkit also provides a passcode retrieval option to access passcode-protected evidence.
ElcomSoft Phone Breaker helps to establish access to password-protected iOS backups, Apple iCloud, Windows Phone and BlackBerry 10 backups. The tool supports fast and handy logical acquisition of data, restores the original password with GPU acceleration or helps retrieve data directly from the cloud.
A couple of years ago, ElcomSoft got overwhelming coverage in global news when its software was misused by hackers to expose a celebrity’s nude selfies grabbed from Apple iCloud. Paradoxically, the FBI and CIA tend to employ the same tools for their causes.
Oxygen Forensic Suite
Oxygen Forensic Suite is a solution designed to collect evidence from mobile devices to support your investigation cases. The software gathers versatile data (OS, manufacturer, IMEI number, serial number), messages (SMS, MMS, email) and contacts.
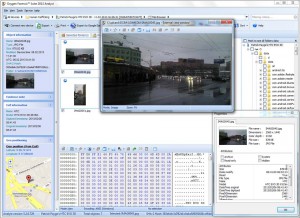 Using Oxygen Suite, you can recover removed messages, call logs and calendar info, as well as access mobile device data and documentation. All gleaned information can be visualized in granular reports, in case you need to see the big picture.
Using Oxygen Suite, you can recover removed messages, call logs and calendar info, as well as access mobile device data and documentation. All gleaned information can be visualized in granular reports, in case you need to see the big picture.
Unlike many competitors who focus on market leaders only, Oxygen Forensic Suite supports a large number of devices based on iOS, Android, Windows Phone, BlackBerry and Symbian operation systems. Similar to ElcomSoft, Oxygen provides cloud-forensics services acquiring data from iCloud, Google and Microsoft Live. Oxygen Forensic Suite is easy to use, yet offers powerful controls, such as the ability to pull data from multiple mobile devices at the same time.
As with many forensic tools, Oxygen provides a timeline feature to glean the culprit’s habits, whereabouts and communications prior to or during the incident. In addition, the Social Graph feature helps to quickly detect evidence and unveil social connections between multiple devices. Oxygen supports data parsing for 300+ unique apps to analyze communication and shared content, and effectively recovers SQLite database records.
These four merited solutions conclude the first part of our forensic tool roundup. The review is to be continued in the next blog posting. Stay tuned for Part 2, and feel free to share your feedback!