A key instrument for event logs analysis is the function of event filtering. All known event log analysis tools have filtering feature, and I suppose, it is the most demanded feature of these applications. Setting filter for the most of event fields is easy. As a rule, all the event log applications let you filter by timeframe, event level, source, event IDs, users or computers with a more or less friendly user interface.
However, sometimes you may need to filter events by extra details, which you can see in the event description. Let’s take the task of displaying logon events from RDP users. Previously I described how to display all the logon events, but now we need to make a more complex filter.
We know that logon events are 4624 and 4625 (successful logon and unsuccessful logon attempt). In this post, I showed how to interpret logon types and you can see that Logon type for RDP access is 10. So we need to filter by event ID= 4624 or 4625 and Logon type = 10. And this filter should be applied to Security log.
Although Windows Event Viewer does not provide user interface to filter events by extra event details, you can query event log by using structured XML queries. This feature is available since Windows 2008/Vista. Structured XML query is a special language based on XPath 1.0 syntax intended to retrieve events from event logs. You can find information about the structured XML queries and XPath expressions at https://msdn.microsoft.com/en-us/library/windows/desktop/dd996910(v=vs.85).aspx
Here is a XML filter query for our task:
<QueryList>
<Query Id=”0″ Path=”Security”>
<Select Path=”Security”>
*[System[(EventID=4624 or EventID=4625)]]
and
*[EventData[Data[@Name=’LogonType’] and Data=10]]
</Select>
</Query>
</QueryList>
Using the power of XML query, you may filter events by virtually any criteria. Our Event Log Explorer “understands” the structured XML queries as well as built-in Event Viewer. But unlike Event Viewer, you don’t need to use full XML queries. Event Log Explorer accepts short XPath expressions like:
*[System[(EventID=4624 or EventID=4625)]] and
*[EventData[Data[@Name=’LogonType’] and Data=10]]
However, despite the advantages of XML filtering, it is not easy to use it, especially if you don’t used to write XML queries on a regular basis.
So now, I will show how we simplified this process with our software.
Select View->Filter from the Event Log Explorer main menu to display Filter dialog.
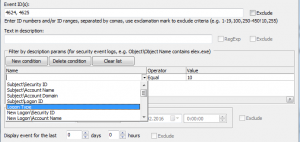
First of all, you should type 4624,4625 into Event ID(s) filed because we need only logon events.
Event Log Explorer provides two basic ways of filtering events by description.
Filtering events by description text
You can just type any text in “Text in description” field and Event Log Explorer will display all events that contain this text in the description. You may just try to type
Logon Type: 10
And this MAY really work. However, it is not reliable at all. You should not rely on the number of tabs inside description, moreover you cannot just type the tabulation symbols in the input line (I pasted it from the event description, and you should not copy it from this article – it won’t work – there are three tabulation symbols between “:” and “10”). Thereby, I suggest using this simple way, only for simple filters, e.g. when you need to display events containing a specific file name in the description.
The same “Text in description” filed has an extra feature when you enable RegExp checkbox near it. In this case, you can filter events with the power of regular expressions. When RegExp checkbox enabled, Event Log Explorer will search all event descriptions for occurrence of the regular expressions you typed in “Text in description” filed. Our expression should look like
Logon Type:\s*10
or
Logon Type:[ \t]*10
You probably think that this way is not much better than using structured XML queries. Instead of learning XPath syntax, I recommend you to learn regular expressions?
Although I don’t see alternatives to regular expression filters for some specific log analysis tasks, Event Log Explorer lets you fulfill this very task (displaying RDP logon events) much easier.
Filtering events by description parameters
Event Log Explorer gives you a user friendly ability to filter Security log by description parameters. In fact, you just tell the program the following:
Logon type equals 10
To make entering the filter condition easy, I recommend select an even in the event list that contains Logon type in the description (you should do this before opening Filter dialog).
Use Filter by description params group to create your filter conditions:
I believe that this way significantly saves your time for security log analysis.
Note that this approach works only when you analyze Security event logs because the security log descriptions are well-structured. When you analyze other logs, you may need to use regular expressions or XPath filter queries.