Several days ago, we published a preview of the new edition of Event Log Explorer software – Forensic Edition! Here I will show what benefits you can get from this edition. First, I should say that currently it is fully compatible with the standard edition of Event Log Explorer – it uses the same workspace, the same settings and currently the same registration key. By default, it installs itself into another folder, so you can use both editions concurrently. By the way, the forensic edition preview is available at
http://eventlogxp.com/download/elex_fe_setup.exe
What should you pay attention to?
You can find a new button on the tool bar ![]() – Add imaged computer.
– Add imaged computer.
How it works. When you have a forensic image, you can mount it as a disk on your computer. And this command lets you add this imaged computer to the tree, and then view event logs from it.
Example:
I currently don’t have forensic images, but I have an old hard drive and connected it to my computer for tests. It is drive E:. I click “Add imaged computer” button and get this dialog:
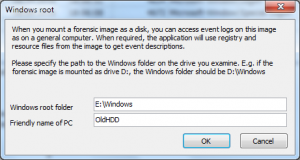
Event Log Explore tries to detect a mounted system drive automatically – it found it in my case, but if it wouldn’t find, just type correct path to the Windows folder on the mounted disk.
Type any name in “Friendly name” field, and press OK.
Now you can see that this “computer” has been added to the tree and you can open it and view event logs.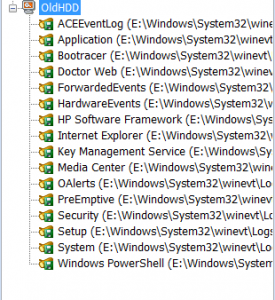
Let’s try to open any log from this imaged computer, e.g. Application. Double click on Application and the event log will appear as a log file.
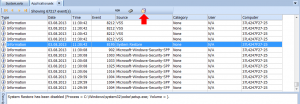
Pay attention to the icon that appears on the log icons area. Commonly it appears when you set a description server. But now it notifies you that Event Log Explorer will try to get descriptions from the mounted disk, when if it failed to find them locally. Whenever Event Log Explorer tries to get event description, it will try to get it locally first (as always), but if the description is not available, it will open registry on the mounted disk, find a resource file that contains event description and try to extract the description from this file. Note that if you research this disk not only with help of Event Log Explorer, but with e.g. Registry Editor and opened registry files (loaded them as hives), you should unload the hives, or Event Log Explorer won’t be able to open them. If you want disable getting descriptions from the imaged computer, just double click on that icon and uncheck “If no description available, get it from imaged disk” option.
What else
We disabled functionality that lets you modify event logs, such us clear log command, modifying event log properties.
What’s next?
We are planning to add the following features to forensic edition:
- Timeline creation
- Opening heavily damaged evtx files
- Opening evt and evtx fragments
- Features you will requested to add!