Sometimes you may need to display who logons your server except for the authenticated domain users. It could be authenticated users from the trusted domain, local users, system services, etc.
First, we define that we will filter the Security log by Event Id = 4624 (as we did before).
The event description of this event looks like
An account was successfully logged on.
Subject:
Security ID: S-1-0-0
Account Name: –
Account Domain: –
Logon ID: 00000000
Logon Type: 3
Impersonation Level: Impersonation
New Logon:
Security ID: S-1-5-21-3517536955-4254224319-112489931-1107
Account Name: Michael
Account Domain: FSPRO
Logon ID: 017448C0
Logon GUID: {00000000-0000-0000-0000-000000000000}
Process Information:
…
New logon group describes the details of a user who logs on. Let’s display events 4624 where New Logon\Account name is not FSPro. It is very easy to do using Event Log Explorer filter.
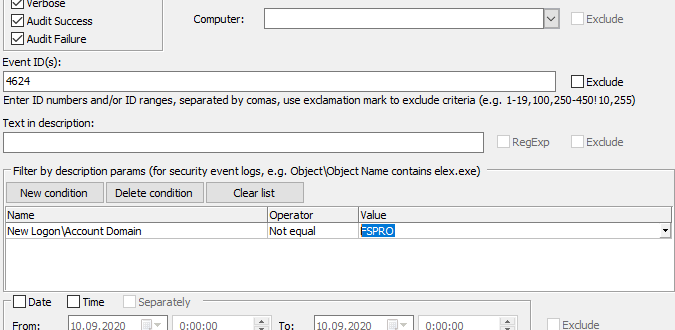
This method works well, but it has several drawbacks:
- Filtering by description params works not so fast – Event Log Explorer parses the description every time and checks its params.
- Filtering by description params depends on the Windows language. In non-English systems, param names like Account Domain could be translated.
- This approach won’t work with Elodea – if you decide to make such a feed.
- It works only with Event Log Explorer. In Windows Event Viewer this or similar functionality is not available.
XML Query doesn’t have these drawbacks, but it’s harder to compose.
Double click on 4624 event and switch to XML tab.
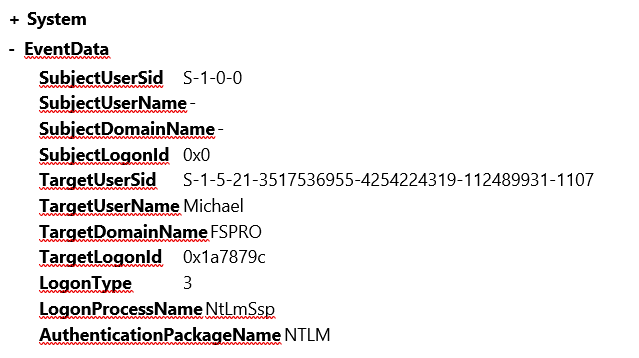
We need to exclude events with TargetDomainName equals to FSPRO.
You may consider that the XML query should look like
<QueryList>
<Query Id=”0″ Path=”Security”>
<Select Path=”Security”>
*[System[(EventID=4624)]]
and
*[EventData[Data[@Name=’TargetDomainName’] and (Data!=’FSPRO’)]]
</Select>
<Query>
<QueryList>
But this query is wrong. Clause “*[EventData[Data[@Name=’TargetDomainName’] and (Data!=’FSPRO’)]]” will return true in most cases since Data has multi values for the most events.
The correct XML query is:
<QueryList>
<Query Id=”0″ Path=”Security”>
<Select Path=”Security”>
*[System[(EventID=4624)]]
and
*[EventData[Data[@Name=’TargetDomainName’]!=’FSPRO’]]
</Select>
</Query>
</QueryList>
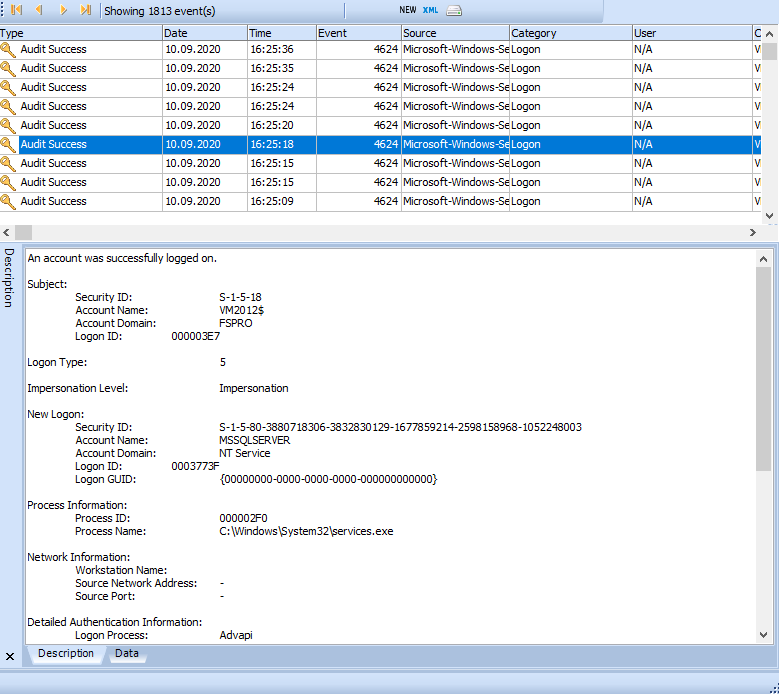
The result of this query:
Download Event Log Explorer right now and try your own event filtering tasks.