Although Standard Edition of Event Log Explorer works with event log files perfectly, you may need more functionality when analyzing damaged or intentionally modified event log files. I’m starting a series of articles about the advanced use of Event Log Explorer Forensic Edition with files.
Let’s imagine that you examine an event log with removed events. If you believe that it’s impossible to remove events from an event log, I will show how to do it.
I will remove logon events from Security event log as follows:
Start Windows Event Viewer.
Open a log file (I take Security.evtx from my old archive, but you can use it even with the live Security log).
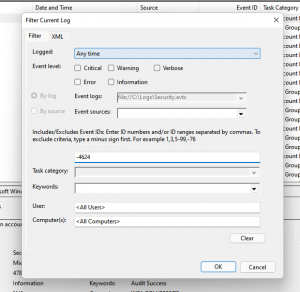
Set Filter in Event Viewer to exclude events 4624 (of course you can set any filter you want).
Click “Save Filtered Log File As” and save it as EVTX file.
Voila, you have a new event log file with removed events. You can open it with Event Viewer or Event Log Explorer and don’t even expect that it’s not an authentic event log. Of course, a real malefactor should replace a live event log with the forged one, but it’s not an impossible task. If s/he has a physical access to the computer, it’s possible to replace C:\Windows\System32\WinEvt\Logs\Security.evtx by loading the computer in recovery console. It’ much harder to forge the log remotely, but still possible by exploiting system vulnerabilities (e.g “Vault 7” hacking tool set lets you exploit such vulnerabilities and remove events).
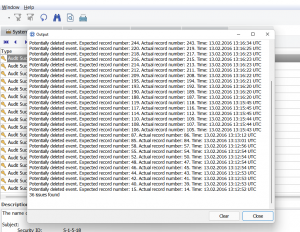
And how can we detect if the examined event log file misses events? We discovered that Event Viewer (more accurately Event Log API) just copies the events into a new file as is. So, all events in the new log file will have the same record number as they had in the original event log. If we scan all the events, we can easily detect missed record numbers.
This functionality is implemented in Event Log Explorer Forensic Edition. Select Forensics from the main menu, click Forensic Open File, add your files by clicking Add button and enable option “Check log files for deleted events”. You will have the list of potentially deleted events.
You may be wondering if it is possible to forge an event log in such a way that it will fix the record numbers making it indistinguishable from non-edited log. It was easy for legacy evt logs, but very hard for the modern evtx event logs. I cannot state that it’s impossible, however I never seen any tools or a sample code that can do such tricks. That’s why I believe that Event Log Explorer can detect events deletion in event logs.
Download Event Log Explorer Forensic Edition and check if your log files have no deleted events!